AppleScript 
- Applescript - copying bold text.pdf
- AppleScript and POSIX paths.pdf
- applescript bold text.JPG
- applescript key code.rtf
- AppleScriptLanguageGuide.pdf
- launching acrobat batch process with applescript - Mac Forums.pdf
- O’Reilly - AppleScript in a Nutshell.pdf
- O’Reilly - AppleScript The Definitive Guide.chm
GIS 
- agentzh-nginx-tutorials-en.pdf
- HttpCoreModule - Nginx Community.pdf
- lion metadata.pdf
- meta mappluto.pdf
- MODEL config.pdf
- ngx eval mod.pdf
- ngx lua mod.pdf
- ngx postgres.pdf
- ngx postgres snip.pdf
- ngx supervisord.pdf
- openresty drizzle-nginx-module.pdf
- openresty DynamicRoutingBasedOnRedis.pdf
- openresty echo-nginx-module.pdf
- openresty lua-resty-upload.pdf
- openresty lua-resty-websocket.pdf
- openresty memc-nginx-module.pdf
- openresty mySQL examples.pdf
- openresty UsingLuaRocks.pdf
- pad info.pdf
- pgRoutingDocumentation.pdf
- pgsql UID.png
- pluto datadictionary.pdf
- postgis-2.1.3.pdf
- postgis cheat sheet.pdf
- QGIS-2.2-UserGuide-en.pdf
- SND metadata.pdf
- SND userguide.pdf
ngx 
- openresty drizzle-nginx-module.pdf
- HttpCoreModule - Nginx Community.pdf
- agentzh-nginx-tutorials-en.pdf
- MODEL config.pdf
- openresty echo-nginx-module.pdf
- openresty lua-resty-websocket.pdf
- openresty UsingLuaRocks.pdf
- ngx postgres snip.pdf
- openresty memc-nginx-module.pdf
- ngx postgres.pdf
- ngx.md
- openresty lua-resty-upload.pdf
- ngx lua mod.pdf
- ngx supervisord.pdf
- openresty mySQL examples.pdf
- openresty DynamicRoutingBasedOnRedis.pdf
- ngx eval mod.pdf
- lion metadata.pdf
- pad info.pdf
- NYC Data.md
- SND userguide.pdf
- meta mappluto.pdf
- SND metadata.pdf
- pluto datadictionary.pdf
JavaScript 
- Acrobat 8 JS API.pdf
- Ajax Simplified.pdf
- Apress.Pro.JQuery.Feb.2012.ISBN.1430240954.pdf
- Practical jQuery.pdf
Update NPM
sudo npm install npm -g
Update Node.js
sudo npm cache clean -f
sudo npm install -g n
sudo n stable
sudo ln -sf /usr/local/n/versions/node/<VERSION>/bin/node /usr/bin/node
node -v
Log Aggregation and Tools 
GrayLog2 (server & interface)
wget http://packages.graylog2.org/releases/graylog2-setup/graylog2-setup-0.92.1.tar.gz
wget https://www.graylog2.org/download/release/graylog2-server/548a1deae4b0a06d87eea030
wget https://www.graylog2.org/download/release/graylog2-web-interface/548a1deae4b0a06d87eea030
Documentation:
https://www.graylog2.org/resources/documentation/setup/quicksetupapp
logstash, elasticsearch, kibana
Splunk
graylog2
loggly
logfaces
fluentd
Kafka
syslog-ng => rabbitmq => elasticsearch
syslog-ng + patterndb
Manuals 
- bike parts.pdf
- casio qw5122.pdf
- EPOCUserManual2014.pdf
- fx260 training guide.pdf
- Inspiron 8600 - Diagrams.pdf
- iPaq h1910.pdf
- Kwik instr.JPG
- LIT-11616-21-61.pdf
- LIT-11626-21-61 R6all 1457.pdf
- model88cd.pdf
- Moto Elite HZ720 User Guide.pdf
- Motorola-S10HD.pdf
- Phillips BluLight hf3332 60 dfu aen.pdf
- S10HD QSG ENFRES 68014214001b.pdf
- ti83Guidebook.pdf
- voyager-legend ug en-us.pdf
Misc 
- DarwinPorts.JPG
- DarwinPorts - Oreilly.pdf
- dinovo edge battery light.png
- Drive Fitness Test - Hitachi.pdf
- Exponential Integrals.doc
- Haverhillweekday.pdf
- Haverhillweekend.pdf
- Hostels.txt
- housing.txt
- internguide.pdf
- Metric prefixes.png
- Nut and bolts Type-Chart.pdf
- NYC Subway.pdf
- Repairing and Maintaining Your Treadmill.pdf
- Syracuse Campus.pdf
Networking 
Testing
- ipv4.google.com
Options:
https://ef.gy/forwarding-ipv4-to-ipv6
https://www.tunnelbroker.net/ https://forums.he.net/index.php?topic=1994.0 http://checkip.dns.he.net/
git@github.com:craSH/Emissary.git https://vpnstaticip.com/download.php
https://www.onioncat.org/2015/12/evading-firewalls-with-onioncat/#more-149 https://www.onioncat.org/download/ https://www.torproject.org/docs/tor-doc-unix.html.en#using https://trac.torproject.org/projects/tor/wiki/doc/TorifyHOWTO https://www.reddit.com/r/ipfs/comments/5blmf0/ipfs_via_onioncat_and_anonymous_proxy/ https://bluishcoder.co.nz/2016/08/18/using-freenet-over-tor.html
https://www.dd-wrt.com/wiki/index.php/IPv6 https://www.dd-wrt.com/wiki/index.php/IPv6_startup_script
IPv4
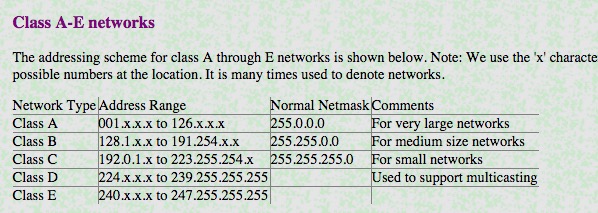
IPv6
ping6 -I en0 ff02::1# identify v6-capable devices on LANtraceroute6ip neighndp -an# (macOS) control/diagnose IPv6 neighbor discovery protocol- MTR
tracepath6
[ -f /proc/net/if_inet6 ] \
&& echo 'IPv6 ready system!' \
|| echo 'No IPv6 support found! Compile the kernel!!'
Tor (info,git) & OnionCat
- port 9050, (9150 for tor web browser)
TunnelBroker
UPDATE
auto-detect ipv4
https://<USERNAME>:<PASSWORD>@ipv4.tunnelbroker.net/nic/update?hostname=<TUNNEL_ID>https://ipv4.tunnelbroker.net/nic/update?username=<USERNAME>&password=<PASSWORD>&hostname=<TUNNEL_ID>
manual ipv4 input
https://<USERNAME>:<PASSWORD>@ipv4.tunnelbroker.net/nic/update?hostname=<TUNNEL_ID>&myip=<IP ADDRESS> https://ipv4.tunnelbroker.net/nic/update?username=<USERNAME>&password=<PASSWORD>&hostname=<TUNNEL_ID>&myip=<IP ADDRESS>
EXAMPLES
curl "https://ipv4.tunnelbroker.net/nic/update?username=sethc23&password=PASSWORD&hostname=382960"
curl "https://sethc23:PASSWORD@ipv4.tunnelbroker.net/nic/update?hostname=382960"
SERVER CONFIG
ip tunnel add he-ipv6 mode sit remote 209.51.161.14 local 66.249.83.220 ttl 255
ip link set he-ipv6 up mtu 1480
ip -6 addr add 2001:470:1f06:1364::2/64 dev he-ipv6
ip -6 route add ::/0 dev he-ipv6
ip -6 addr
ping6 -b -I 66.249.83.220 2001:470:1f06:1364::2/64
Tools
curl
curl --interface 10.0.0.92 http://www.google.comcurl --insecure -L 87.238.57.232
lsof
socat
tcpdump
tcpflow
tcpflow -p -c -i eth0 port 80
(below source obtained 2017.01.13) Get an ip address for en0:
ipconfig getifaddr en0
Same thing, but setting and echoing a variable:
ip=ipconfig getifaddr en0 ; echo $ip
View the subnet mask of en0:
ipconfig getoption en0 subnet_mask
View the dns server for en0:
ipconfig getoption en0 domain_name_server
Get information about how en0 got its dhcp on:
ipconfig getpacket en1
View some network info:
ifconfig en0
Set en0 to have an ip address of 10.10.10.10 and a subnet mask of 255.255.255.0:
ifconfig en0 inet 10.10.10.10 netmask 255.255.255.0
Show a list of locations on the computer:
networksetup -listlocations
Obtain the active location the system is using:
networksetup -getcurrentlocation
Create a network location called Work and populate it with information from the active network connection:
networksetup -createlocation Work populate
Delete a network location called Work:
networksetup -deletelocation Work
Switch the active location to a location called Work:
networksetup -switchlocation Work
Switch the active location to a location called Work, but also show the GUID of that location so we can make scripties with it laters:
scselect Work
List all of the network interfaces on the system:
networksetup -listallnetworkservices
Rename the network service called Ethernet to the word Wired:
networksetup -renamenetworkservice Ethernet Wired
Disable a network interface:
networksetup -setnetworkserviceenabled off
Change the order of your network services:
networksetup -ordernetworkservices “Wi-Fi” “USB Ethernet”
Set the interface called Wi-Fi to obtain it if it isn’t already
networksetup -setdhcp Wi-Fi
Renew dhcp leases:
ipconfig set en1 BOOTP && ipconfig set en1 DHCP ifconfig en1 down && ifconfig en1 up
Renew a dhcp lease in a script:
| echo “add State:/Network/Interface/en0/RefreshConfiguration temporary” | sudo scutil |
Configure a manual static ip address:
networksetup -setmanual Wi-Fi 10.0.0.2 255.255.255.0 10.0.0.1
Configure the dns servers for a given network interface:
networksetup -setdnsservers Wi-Fi 10.0.0.2 10.0.0.3
Obtain the dns servers used on the Wi-Fi interface:
networksetup -getdnsservers Wi-Fi
Stop the application layer firewall:
launchctl unload /System/Library/LaunchAgents/com.apple.alf.useragent.plist launchctl unload /System/Library/LaunchDaemons/com.apple.alf.agent.plist
Start the application layer firewall:
launchctl load /System/Library/LaunchDaemons/com.apple.alf.agent.plist launchctl load /System/Library/LaunchAgents/com.apple.alf.useragent.plist
Allow an app to communicate outside the system through the application layer firewall:
socketfilterfw -t “/Applications/FileMaker Pro/FileMaker Pro.app/Contents/MacOS/FileMaker Pro”
See the routing table of a Mac:
netstat -nr
Add a route so that traffic for 10.0.0.0/32 communicates over the 10.0.9.2 network interface:
route -n add 10.0.0.0/32 10.0.9.2
Log bonjour traffic at the packet level:
sudo killall -USR2 mDNSResponder
Stop Bonjour:
launchctl unload -w /System/Library/LaunchDaemons/com.apple.mDNSResponder.plist
Start Bojour:
launchctl load -w /System/Library/LaunchDaemons/com.apple.mDNSResponder.plist
Put a delay in your pings:
ping -i 5 192.168.210.1
Ping the hostname 5 times and then stop the ping:
ping -c 5 google.com
Flood ping the host:
ping -f localhost
Set the packet size during your ping:
ping -s 100 google.com
Customize the source IP during your ping:
ping -S 10.10.10.11 google.com
View disk performance:
iostat -d disk0
Get information about the airport connection on your system:
/System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport -I
Scan the available Wireless networks:
/System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport -s
Trace the path packets go through:
traceroute google.com
Trace the routes without looking up names:
traceroute -n google.com
Trace a route in debug mode:
traceroute -d google.com
View information on all sockets:
netstat -at
View network information for ipv6:
netstat -lt
View per protocol network statistics:
netstat -s
View the statistics for a specific network protocol:
netstat -p igmp
Show statistics for network interfaces:
netstat -i
View network information as it happens (requires ntop to be installed):
ntop
Scan port 80 of www.google.com
/System/Library/CoreServices/Applications/Network\ Utility.app/Contents/Resources/stroke www.google.com 80 80
Port scan krypted.com stealthily:
nmap -sS -O krypted.com/24
Establish a network connection with www.apple.com:
nc -v www.apple.com 80
Establish a network connection with gateway.push.apple.com over port 2195
/usr/bin/nc -v -w 15 gateway.push.apple.com 2195
Establish a network connection with feedback.push.apple.com only allowing ipv4
/usr/bin/nc -v -4 feedback.push.apple.com 2196
Setup a network listener on port 2196 for testing:
/usr/bin/nc -l 2196
Capture some packets:
tcpdump -nS
Capture all the packets:
tcpdump -nnvvXS
Capture the packets for a given port:
tcpdump -nnvvXs 548
Capture all the packets for a given port going to a given destination of 10.0.0.48:
tcpdump -nnvvXs 548 dst 10.0.0.48
Capture the packets as above but dump to a pcap file:
tcpdump -nnvvXs 548 dst 10.0.0.48 -w /tmp/myfile.pcap
Read tcpdump (cap) files and try to make them human readable:
tcpdump -qns 0 -A -r /var/tmp/capture.pcap
What binaries have what ports and in what states are those ports:
lsof -n -i4TCP
Make an alias for looking at what has a listener open, called ports:
| alias ports=’lsof -n -i4TCP | grep LISTEN’ |
Report back the name of the system:
hostname
Flush the dns cache:
dscacheutil -flushcache
Clear your arp cache:
arp -ad
View how the Server app interprets your network settings:
serveradmin settings network
Whitelist the ip address 10.10.10.2:
/Applications/Server.app/Contents/ServerRoot/usr/libexec/afctl -w 10.10.10.2
and this script: http://fileadmin.cs.lth.se/cs/Personal/Peter_Moller/scripts/network_info.sh
networking notes 
Method for enabling BSD:Syslogs on OSX/macOS to accept incoming connections.
- See [Here](https://superuser.com/questions/131578/how-do-you-enable-syslogd-to-accept-incoming-connections-on-snow-leopard-from-re).
- and this:

Socket Disambiguation
- [Socket keys](osx_changes/socket_keys.png)
Python 
Pip
sudo pip install --pre -e .
- 2013-Lyon Spencer-Capstone.pdf
- 2014.05.10 cython tutorial.pdf
- Beautiful Soup Documentation.pdf
- Beautiful Soup Documentation.skim
- Beautiful Soup PYTHON.png
- cell array.png
- colors.png
- cython-slides.pdf
- django 1.6.pdf
- Euro HPC 2013.pdf
- Euro HPC 2013.pdf
- EuroSciPy2010.pdf
- geopandas.pdf
- good python intro.pdf
- graphing particles.pdf
- HTML form useage.JPG
- html mechanize.pdf
- IPython -Timing and Profiling.pdf
- IPython sheet.pdf
- logistics lecture.ppt
- No.Starch.Black.Hat.Python.Dec.2014.ISBN.1593275900.pdf
- numpy.pdf
- numpy2.pdf
- numpybook.pdf
- pandas cheatsheet.pdf
- pandas cheatsheet.pdf
- polyfit.png
- polyval.png
- postgre array operators.png
- postgre data types.png
- pytest.pdf
- python-strptime.JPG
- python - Dates and Times.pdf
- python excel 08.pdf
- python install.png
- READ–PAGC.pdf
- SciPy2009 proceedings.pdf
- SciPy2009 proceedings.pdf
- smtp2web.com Bridge SMTP to HTTP.pdf
- The Shapely User Manual — Shapely 1.2 and 1.3 documentation.pdf
- urllib2 — extensible library for opening URLs.pdf
Stack 
- Emacs Command Summary.pdf
- github-cheat-sheet-en.pdf
- lua-Lua.Lua.3rd.Edition.Jan.2013.ISBN.859037985X.pdf
-
lua-Lua.Lua.5.1.Reference.Manual.Aug.2006.ISBN.8590379833.chm
- nginx-config_directives.pdf
- nginx-mod-ngx_cosocket_pgsql.pdf
- nginx-mod-ngx_lua_memcached.pdf
- nginx-mod-ngx_request_lifetime.pdf
- pgSQL-date patterns.pdf
-
pgSQL-Packt.PostgreSQL.Server.Programming.Jun.2013.ISBN.1849516987.pdf
- syslog-ng-A_How_to_Guide_on_Modern_Monitoring_and_Alerting_-_DevOps.comDevOps.pdf
- syslog-ng-3.0.pdf
- syslog-ng-3.6.pdf
- syslog-ng-tutorial-mutual-auth-tls.pdf